Introduction
In this article "process" and "application" has the same meaning. When expressing as a process it means that is running in the OS, and when expressing it as an application it means the program itself.
Also, basic knowledge on virtual memory is required, please refer to the following.

About memory protection within process
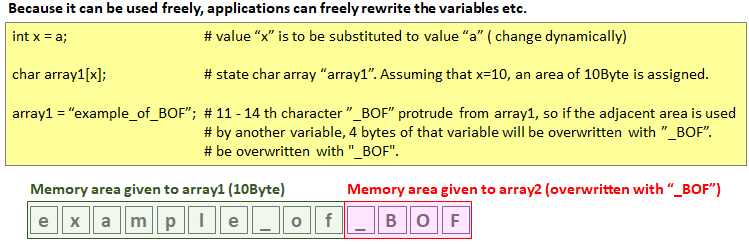
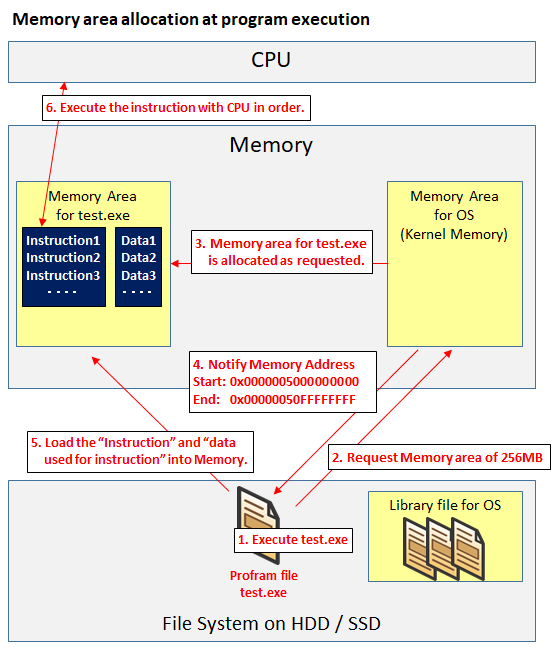
At applications startup, the memory area (virtual address) is assigned. Applications are free to use within the range of given memory, but because they are free, they are vulnerable if you do not properly manage memory by programming.
The most famous is the buffer overflow attack. This means that after allocating a memory address for an array, if there is an assignment exceeding the array size , even the stack area will be overwritten.
In the above example, we just put a character string, but you can also enter commands freely.So, for example, if you assign "instruction" and "return address to that instruction" to that variable as a set, you can execute illegal instructions in the application.
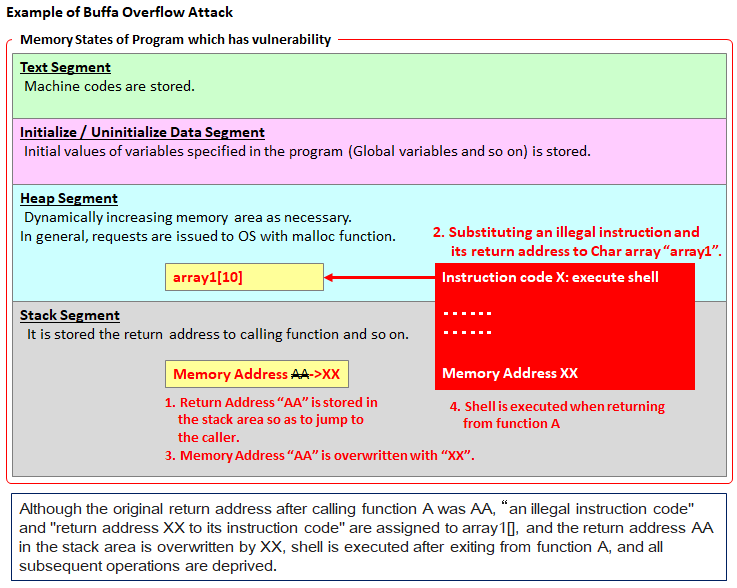
The following is an image when a buffer overflow attack is received on a vulnerable program.
Programs written in C language are divided into the following four areas in memory.
- Text Segment
: Machine codes are stored. - Initialize/Uninitialize Data Segment: Initial values of variables specified in the program (Global variables and so on) is stored.
- Heap Segment: Dynamically increasing memory area as necessary. In general, requests are issued by application to OS with malloc function.
- Stack Segment: It is stored the return address to calling function and so on.
In the above example, the array "array1" arranged in the Heap area stores "an instruction code" generally called a shell code "and" a memory address at which the instruction code is stored "(that is, array1[0] Memory address) "is assigned.This overflows from the Heap area and overwrites the return destination address from the function A in the Stack area. And when the program tries to return from the function A to the caller in execution, it should go back to "AA", it returns to "XX", and the shell is activated.If this program is running as root, it will become ready to operate the shell with root privileges.
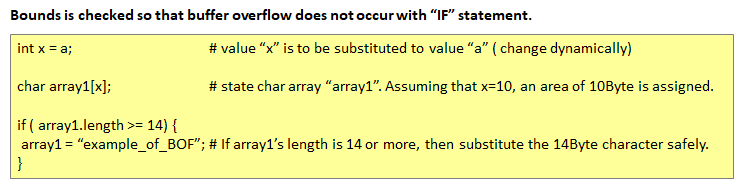
For this reason, when programming, it is common sense as a method of practice to prevent assignment exceeding the size allocated to an array etc. from occurring.
In Specter's attack, it is indicated that malicious code is embedded in a normal application that is applying Bounds Check, and information in the application is pulled out by passing through this Bounds Check.
About memory protection between processes
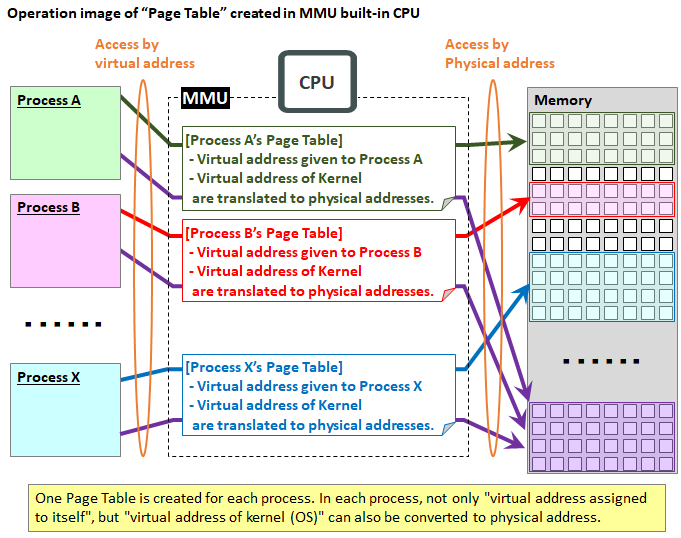
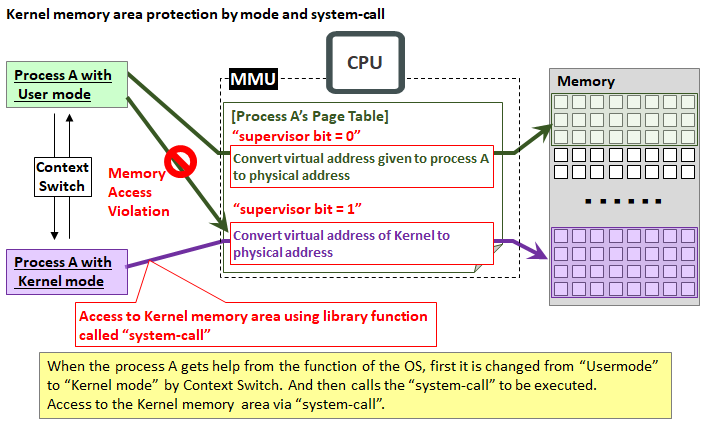
It is job of the MMU (Memory Management Unit) incorporated in the CPU to manage the memory area so that multiple processes do not erode each other's memory area.
The memory area protection within the process must be done by the application itself (that is, by the programmer), but in the case of memory area protection between processes, OS and MMU cooperatively protect.
Specifically, each process has its own Page Table in the MMU. The Page Table converts the virtual address understood by the process into the physical address that the memory actually has. With this Page Table, processes are protected from entering each other's physical address space.
But there are exceptions. It is a kernel (OS) memory area.
Each process runs on the OS and operates with the help of the OS, so you need to be able to access the memory area of the OS. Because there are many things that are often required the OS help, in addition to the memory area given to the application itself, the kernel memory area is commonly provided in the Page Table in consideration of performance.
However, since it is dangerous as it is, access is permitted only when the CPU is operating in kernel mode (supervisor mode) by attaching supervisor-bit to the page of the kernel memory area of the page table (for example, Windows PC It is called "administrator authority").Attempting to access in user mode will be treated as "memory access violation" (normally the process will stop). Switching between user mode and kernel mode is carried out by "Context Switch" which is used for switching the execution process of the multitasking OS.
Also, since you are in supervisor mode , it does not mean you can access everything. You need to use library functions prepared for OS access such as system calls.
By doing this, it is protected so that applications not knowing what programmers made can arbitrarily not enter the kernel memory area.
KAISER (KPTI) which was implemented before Meltdown's announcement
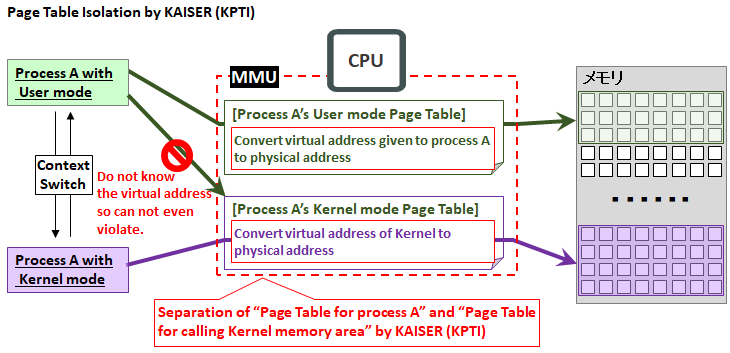
Until the first half of 2017, this page table was only one in each process.In other words, the virtual address for the application and the virtual address of the kernel area used one page table.
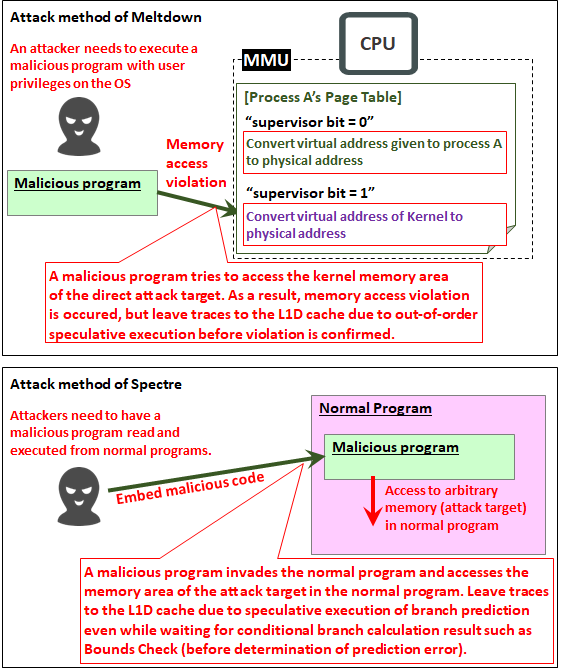
However, due to the appearance of Meltdown this time , the situation changed.It is because it was known (to some parties before the announcement) that it is possible to observe the kernel memory area by side-channel attack of the application, which hit the security hole of out-of-order execution implementing speculative execution.
This attack was that the user mode process only tried to access the kernel area (which is a violation of the access right), but it was a violation, but a trace could be left in the L1D cache.
So the countermeasure launched promptly is " KAISER (Kernel Address Isolation to have Side-channel Effectively Removed) " (reading: Kana).This is a function to divide the page table into two, manage one for that application, and the other for calling the kernel memory area.
In this way, in the user mode, we created a state where even "memory access violation" can not be done in the kernel memory area.
This KAISER quickly changed to the name KPTI (Kernel Page-Table Isolation).
Essential difference with Specter
From the above, Meltdown has the following features.
- It happens by executing a malicious program on the OS
- Directly access the kernel memory area which is visible from the Page Table but which violates the access right
- Although it becomes a memory access violation, trace can be left in the L1D cache by the speculative execution function, so attacker can know the memory area you tried to access based on the trace
On the other hand, the essence of Specter's attack is not to read the kernel memory area. As a generic explanation, "Embed malicious programs and scripts in one normal application and read in the memory area in the normal application by observation".
As a specific example, you can say "Embed malicious JavaScript code in a Web server, load it from a normal application called Firefox and execute it, and read the password storage area from Firefox by observation".
A further horrible thing about Specter is that " users can access the kernel area with the eBPF interpreter that can run with kernel privileges " or " The root privilege of the virtual server lent from the cloud provider, It can read the kernel area of the virtual host managed by the virtual host or the kernel area of another user's virtual server".
In other words, if you use a tool (eBPF or KVM) that allows users to run with kernel privileges (= root privileges) as an implementation of attacks, you can do something like Meltdown "without memory access violation" (Having kernel privilege / root privilege, it does not violate that point) " can be executed.
As you can see from these, KAISER/KPTI which is made as a countermeasure of Meltdown can not be a workaround for Specter.
Summary
I summarized the points of commonality and difference between Specter and Meltdown.



コメント