What is Stateful Inspection
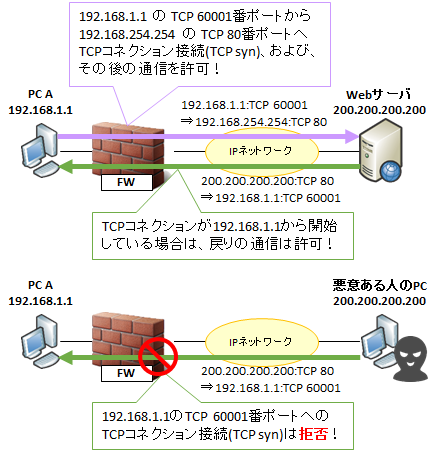
Stateful Inspection is a mechanism that manages TCP connections and UDP (DNS, NTP, etc.) that is required for round trip , and dynamically allows return communication.Considering communication as a conversation with the following figure as an example, when talking to the Web server from host A, the Web server can reply to host A.However, the web server can not speak to host A.
That is, even if communication from the PC A to the Web server on the Internet ( TCP port 80 of arbitrary IP) is permitted, a malicious person attempts to start communication by setting the TCP source port 80 Communication can be prevented.
TCP bidirectionally connects TCP connections, so return communication always occurs. When deciding the policy (access control rule), it is quite difficult to define this return communication. This is because TCP client communication often uses random ports of 1024th and subsequent ports at random, so it can not be decided in advance. In addition, UDP, DNS, NTP, etc. may require return communication, but similarly, it is difficult to define them beforehand.
Therefore, we managed a TCP connection and UDP reciprocation, and dynamically allowed return communication. This function is stateful inspection.
A single go-around communication and the pattern of communication dynamically allowed thereby are collectively called a session. In addition, the method of maintaining security by sessions is called " session management". A TCP connection is counted as one session, and DNS and NTP where round trip is also required for UDP are counted as one session in one round-trip.
Stateful inspection example
The behavior of stateful inspection has almost the same behavior in what kind of firewall (Cisco 's ASA, PaloAlto, FortiGate, SSG etc).
In stateful inspection, not only TCP but also various protocol behaviors are grasped, and it is designed to be dynamically allowed according to its context (in the context of conversation, the context).For example,
- In UDP , return communication occurs with many protocols such as DNS and NTP, but they are managed as sessions (also called UDP virtual connections) like TCP, and return communication is also dynamically permitted can do.
- If the communication is abandoned on the intermediate NW device, ICMP error is notified to the sender, but you can also dynamically allow this ICMP error ( Time Exceeded , Destination Unreachable etc).
- In FTP, if you are in Active mode, you come up with a session from the server, but this is allowed dynamically. Of course also dynamically determined is file transfer port number of the Passive mode, and dynamically open by looking at the communication contents.Dynamically allow other protocols that use other dynamic ports as well.However, since the corresponding protocol differs depending on the device, confirmation is necessary in advance.
In other words, talks with no context are blocked, but the conversation involved as a series of flows is continued.
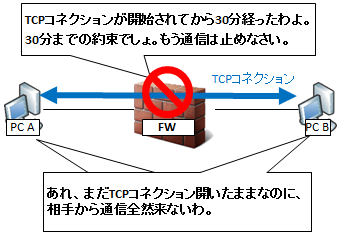
Session timeout
By the way, it is good to dynamically allow returning TCP / UDP communication, but if you continue to allow it forever, it will become a security hole that allows intrusion from malicious ones.Therefore, it is necessary to decide the time to allow beforehand.This time is called session timeout, and even if the host maintains a TCP connection even after the session timeout, the FW during that time will discard the communication.As a result, TCP timeout also occurs on the application side of the PC, and the connection is closed by TCP Reset, TCP Fin etc.
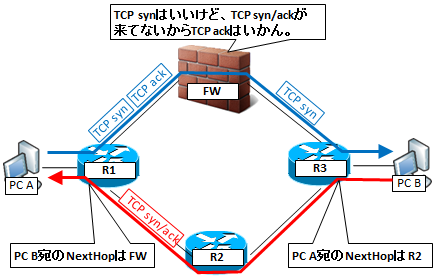
Asymmetric Routing
Because the role of IP is only the route instruction to the destination IP, it is not guaranteed that the outgoing route and return route will be the same.There is no problem if there is no FW on the route, but FW is problematic because we are seeing the round trip of communication for the stateful inspection function.
Specifically, if TCP syn comes but TCP syn / ack can not be seen and TCP ack is attempted to be returned, or conversely TCP su / ack came suddenly, the packet is discarded.
コメント