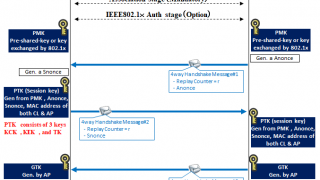
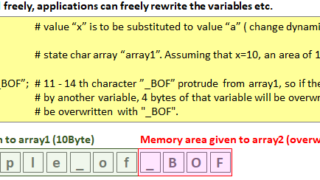
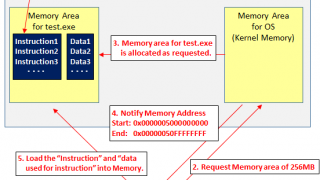
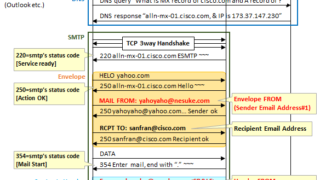
 NW Security
NW SecurityMechanism of outgoing e-mail address impersonation [Mailsploit] ~ Basic e-mail anti-spoof technology SMTP AUTH, DKIM, SPF / SenderID overview (merit · demerit) Commentary and relation with this attack-
What is Mailsploit?Mailsploit is an atta...