Man in the Middle attack of Wi-Fi
The vulnerability of WPA2 [KRACK] became a hot topic the other day (October 16, 2017), but as I investigated the attack, found that Man in the Middle attack on wireless is being used.
"How does KRACK allow wireless frames decrypted specifically" is here.
If it is wired, it is famous for ARP poisoning that spoofs the MAC address of the default gateway with the MAC address of the attacker, but this can not be used for wireless.
Instead, there is a channel-based Man in the Middle attack, and it seems that it is used in the vulnerability of WPA2, so I investigated the outline.
Overview of Channel-based MitM
The mechanism of Channel-based MitM was simple as long as it was made familiar. Follow the steps below to execute the attack.
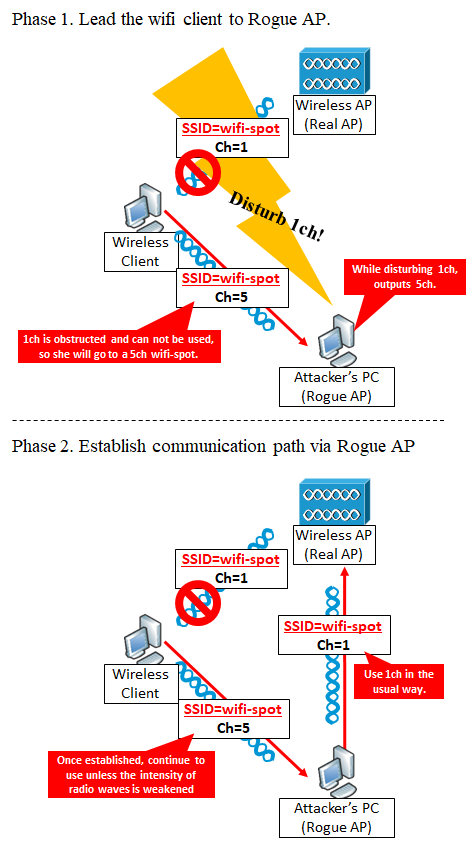
Phase 1. Initiate wireless client to Rogue AP
The attacker PC picks up the SSID of the wireless AP (Real AP) he wants to intervene and continues to output jamming waves of the wireless channel (eg, 1 ch) output by this Real AP so that the client PC can not connect to the Real AP I will. At the same time, the attacker's PC outputs the SSID of the Real AP on another radio channel (for example, 5 ch), outputs a radio wave as a fake radio AP (Rogue AP), guides the radio client to the 5-ch WiFi radio I will.
Phase 2. Establish communication via Rogue AP
Generally, when wireless clients connect once to an SSID of a certain channel, unless the intensity of radio waves becomes lower than a certain threshold value, the wireless clients continue to use the SSID of the channel. So once the wireless client has established a wireless link to the Rogue AP, will stop jamming radio waves, and as a result, uses 5 ch between wireless client and Rogue AP, and uses 1ch between Rogue AP and Real AP.
References
[1] Mathy Vanhoef and Frank Piessens. Advanced Wi-Fi Attacks Using Commodity Hardware, 2014.
コメント