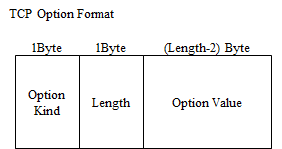
TCP options is represented as following format.
There are mainly seven kinds of TCP options. It is shown below.
0.End Of Option List
1.No Operation
2.MSS(Maximum Segment Size)
3.Window Scale
4.SACK (Selective ACKnowledge) Permitted
5.SACK
8.Time Stamp
Explanation of each option
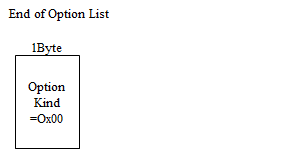
End of Option List
Kind number 0. All bits of 1Byte are assigned by 0. This indicates the last of options. However, it seems there is hardly implemented in actual.
No Operation
Option Kind Number 1. It is used as delimiter between options and padding for making whole TCP header is alligned to a multiple of 4. For example, in case using SACK(Kind Number 5), if SACK is 10 Byte, then 2 No-Operation (2 Bytes) are between TCP header and TCP options as delimiter and padding, and following the SACK(10 Bytes), so the sum is 12 Bytes(multiple of 4 Bytes).
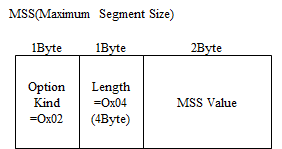
MSS
Option Kind Number 2. It is used for negotiations the maximum size segment which it is abled to receive each other, while 3way handshake's syn and syn/ack.
If MTU value of host is 1500 Bytes(in most case is so), since IP header length and TCP header length is 20 Bytes without options, then it is negotiated by 1460 Bytes each other.
It should be noted the WAN circuit is not necessarily so. For example, NTT's flet's line is limited the MTU value to 1454 Bytes, so you should set the mss value to 1414 Bytes. (fragmentation is not permitted by Path MTU Discovery) So, most routers implement the function of changing the mss value by overwriting this option value while 3way handshake.
For example, cisco realizes this following command.
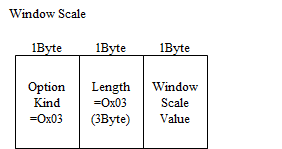
Window Scale
Option Kind Number 3. TCP Window field can tell the opponent how many Bytes up to 64K Bytes he can receive, but considering the specification of recent host machine, it is not sufficient. So the extention had been done by this option as more than 64K Bytes.
You can shift the scale of the Window Field bit by the number specified by this Window Scale.
For example, if Window Scale is set to 1, Window field can be represented up to 2 to the 17th power = 128K Bytes. Similarly, if set to 4, it can be up to 2 to the 20th power = 1M Bytes.
Window scale value can be from 0 to 15.
In addition, this option also is used while 3way handshake's syn and syn/ack, like mss. But it is not negotiation, each host can set different value.
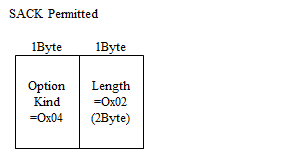
SACK Permitted
Option Kind Number 4. It notifies SACK(Selective ACK) supported. This also is used while 3way handshake's syn and syn/ack.
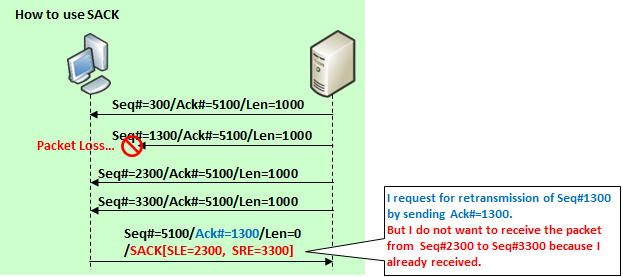
Before appearing this SACK, TCP receiver watches Seq# and if detects packet loss, reply with Ack# for just before lost packet, and TCP sender retransmits not only lost packet but also all packets after lost. So it is inefficient that receiver takes already received one twice or more.
But by appearing SACK, this problem is solved. For specific method, see the next item.
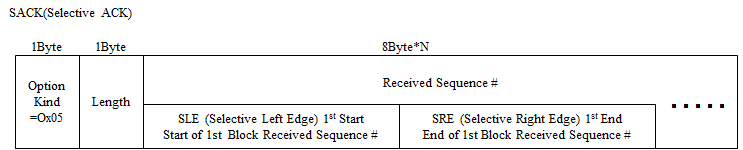
SACK
Option Kind Number 5. The TCP connection which each host presents "SACK Permitted" option, can retransmit only lost packet(s) as following method.
TCP receiver watches Seq# and if detects packet loss, reply with Ack# for just before received packet with this option which includes start Seq# of lost packet and end Seq# of one.
It will be shown below how to use SACK.
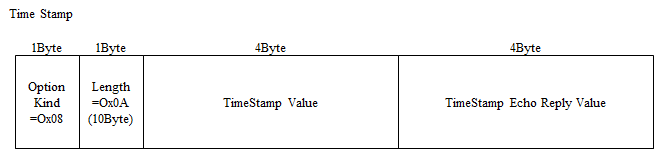
Time Stamp
Option Kind Number 8. TCP's retransmit time is calculated based on RTT(Round Trip Time) value, which is average time from transmitter sending to transmitter receiving reply. This RTT value is calculated by sampling 1 packet per window size.
When Window size's maximum was 64K Bytes, it was not so worse, but by introducing "Window scale" option, as the scale is larger, accuracy of RTT is even worse.
To respond to this, "Time Stamp" option is used. By hosts presenting this option while 3way handshake, they can calculcte RTT anytime using this option's value while the TCP connection.
Host B who received the TCP segment with "TS" field from Host A, is set "TS echo reply" field to received "TS" value, and is set "TS" field to time to send to Host A as reply.
In addition, recently it is natural to use 1Gbps network, and it is expected that Seq# goes around for about 40 seconds at the worst case.
If packets are delayed, it is possible to duplicate the Seq# by going around. So, the solution called PAWS (Protection Against Wrapped Sequence) appears. this is the method that Seq# with Time Stamp option avoids duplication. By this, hosts identify the newer packet from older packet.
However, this Time Stamp option is indicated the vulnerability of DoS, so it is important to prepare the proper environment such as which packet is not able to guess, or is pass through firewall, if you want to enable this.


コメント