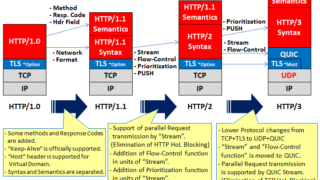
 http
http[Illustration] How does HTTP/3 (HTTP over QUIC) work?〜Advantages of UDP, differences between versions(v1.0/v1.1/v2/v3)〜
The HTTP protocol has contributed to the...
 http
http Windows Basic Knowledge
Windows Basic Knowledge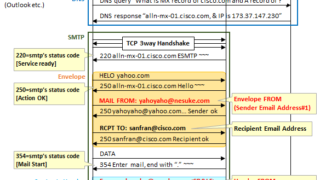 NW Security
NW Security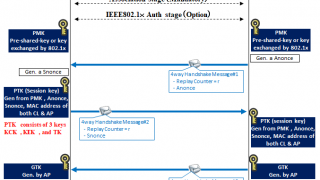 NW Security
NW Security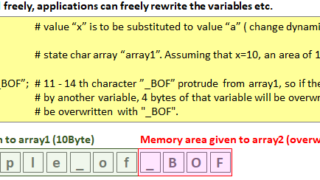 NW Security
NW Security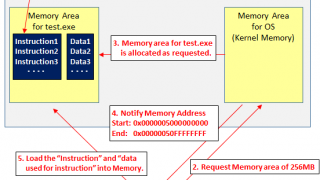 NW Security
NW Security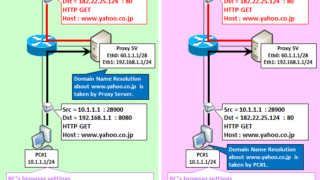 Server Software
Server Software DNS
DNS